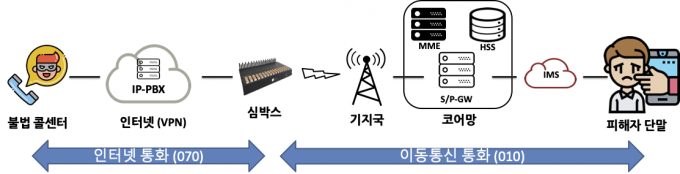
– Professor Yongdae Kim’s team develops a detection technology to distinguish benign mobile phones and SIM boxes used for malicious voice phishing over LTE.
– This technology differentiates between the SIM boxes and mobile devices based on the unique characteristics of each mobile device.
– It is necessary to implement a SIM box registration system, which is expected to effectively block voice phishing crimes in the future.

[Professor Yongdae Kim]
If SIM boxes are exploited for voice phishing, it is possible that internet calls from overseas can be used to manipulate the calling number to be recognized as a number coming from within Korea. Professor Yongdae Kim’s team from the School of Electrical Engineering has developed proprietary technology which identifies SIM boxes used for voice phishing by mobile carriers. All devices, including mobile phones, transmit the features that they can support when connecting to a mobile communication network. Professor Yongdae Kim’s team proposed a method of distinguishing mobile devices using around 1,000 of such features and was able to classify models of around 100 mobile devices. They also confirmed that this technology can clearly distinguish between SIM boxes and benign mobile phones.
Beomseok Oh, a researcher at KAIST and the co-first author of this research, said, “We confirmed that the mobile phones and SIM boxes can clearly be distinguished using over 100 mobile devices.” He added, “to apply this technology in real life, we need to collaborate with the mobile carriers for verification using commercial data and further technological advancement.”
Professor Yongdae Kim said, “there also exist legitimate use of SIM boxes, which means that it is important for mobile carriers to not only detect SIM boxes, but to identify those that are being used in a malicious manner.” He further explained, “to effectively apply this technology, a SIM box registration system is needed. SIM boxes used for legitimate purposes can be registered as such, while unregistered SIM boxes can be identified as being illegally used.”
[related press]
(Yonhap News Agency ) : ‘보이스피싱 꼼짝마’ KAIST, 불법 중계기 탐지 원천기술 개발 | 연합뉴스 (yna.co.kr)
(Dong-A Science Co., Ltd ) : 보이스피싱 악용되는 ‘국제전화번호 변환’ 탐지 기술 개발 : 동아사이언스 (dongascience.com)
(the economy of Ajou ): KAIST, ‘심박스’ 탐지 원천기술 개발… 보이스피싱 예방 기대 | 아주경제 (ajunews.com)